by Paul Matthews, CEO

“Hacking” is certainly nothing new and up until relatively recently, was seen by many as simply an inconvenience. Often it would involve enduring nothing more serious than a relatively harmless – but highly embarrassing – website defacement.
Not now, however.
These days, the bad guys mean business. Companies all around the world face devastating consequences: pay us a big sum of money or we’ll destroy you. And often they really mean it, as a number of healthcare and other organisations have found out recently.
But to understand how we got to the situations we’re in now around hacking, let’s delve into the backstory a bit.
A brief history of hacking
The first “hack” ever recorded was a case of simple industrial vandalism. Back in 1903, Nevil Maskelyne, a manager from the Anglo-American Telegraph Company, hacked the transmission demonstration of a rival technology he saw as a challenge to their humble telegraph tech.
And it kind of worked – the telegraph remained a technology staple right up until the last telegraph was sent more than a hundred years later, in 2006. His target though, Guglielmo Marconi, won the 1909 Nobel Prize for Physics and had major success inventing the radio, so it’s not all bad news.
Fast forward to the late 60s, where MIT became the “base” for a new generation of “hacking”; however, it was a force for good – often hacking software to make it run better (albeit via unauthorised changes). This was essentially the spiritual beginnings of Free and Open Source Software (FOSS) movement, where anyone can make code better.
Hacking as we know it today really started in the late 1960s, with the first “big” unlawful hack being John Draper’s phone phreaking – manipulating phones to make free long-distance calls. A version of this (called tapping where you’d tap 10 minus the number you’re trying to call) was still in play when I was a kid, meaning some of the more naughty neighbourhood kids could make free calls from public telephones.

During the 1980s, hacking in its traditional form reached an all-time peak. A combination of the trend from big mainframes to personal computers, combined with the reshaping of the Internet, created big opportunities for some curious but nefarious geeks. People like Bill Landreth went to jail for hacking both NASA and the Department of Defence.
It was also during this time that the first “Ransomware” viruses emerged, encrypting files and requiring payment to be sent through the postal service. These weren’t overly effective, and it really wasn’t until the advent of cryptocurrencies in the 2010s that enabled the payment problem of ransomware to be solved.
The Great Hacker War
The “Great Hacker War” in the later 80s and early 90s saw hacker groups the Legion of Doom (LOD) and spin-off Masters of Deception (MOD) try to one-up each other with high volumes of targets, until many of them were sent to jail.
These types of hacks continued for some time, mostly for notoriety and reputation than financial gain. There were some exceptions – such as the Hao twins in China being sentenced to death in 1998 for hacking a bank and stealing 720,000 yuan.
It was around this time that things started to change, and computer viruses and “worms” began to take on a more significant, and damaging, bent. Viruses such as CIH and Melissa started causing real damage, the first by impacting PC hardware, and the second by overloading email servers worldwide with the first big email-borne worm.
This was followed by a decade of worm-style viruses in the 2000s, with worms like CodeRed, Netsky, Sasser, and more causing all sorts of havoc. Again, while costly and destructive, most were without a financial motive.
However, the number of financial-related hacking attempts started to increase markedly with gangs hacking banks, ATMs, and even charity efforts (e.g. redirecting donations to Red Cross to personal bank accounts).
But it’s in more recent times that things have got really serious.
Ransomware is big business now
Ransomware, where a virus or hackers encrypt systems and refuse to release data unless a ransom is paid, really only started coming of age in around 2012. Today it’s arguably the largest threat to business – certainly online business – worldwide.
Gone are the days when script kiddies looking for notoriety were the prominent attackers – teenagers in the proverbial parent’s basement using tools created by others to get their name out there. These days, Ransomware is organised and it’s big.
If it feels like you’re always hearing about ransomware, it’s because you are. In fact, ransomware has seen exponential and explosive growth, with 80% more attacks this year than last and growing fast. Next year, ransomware will cost business $42 Billion USD.
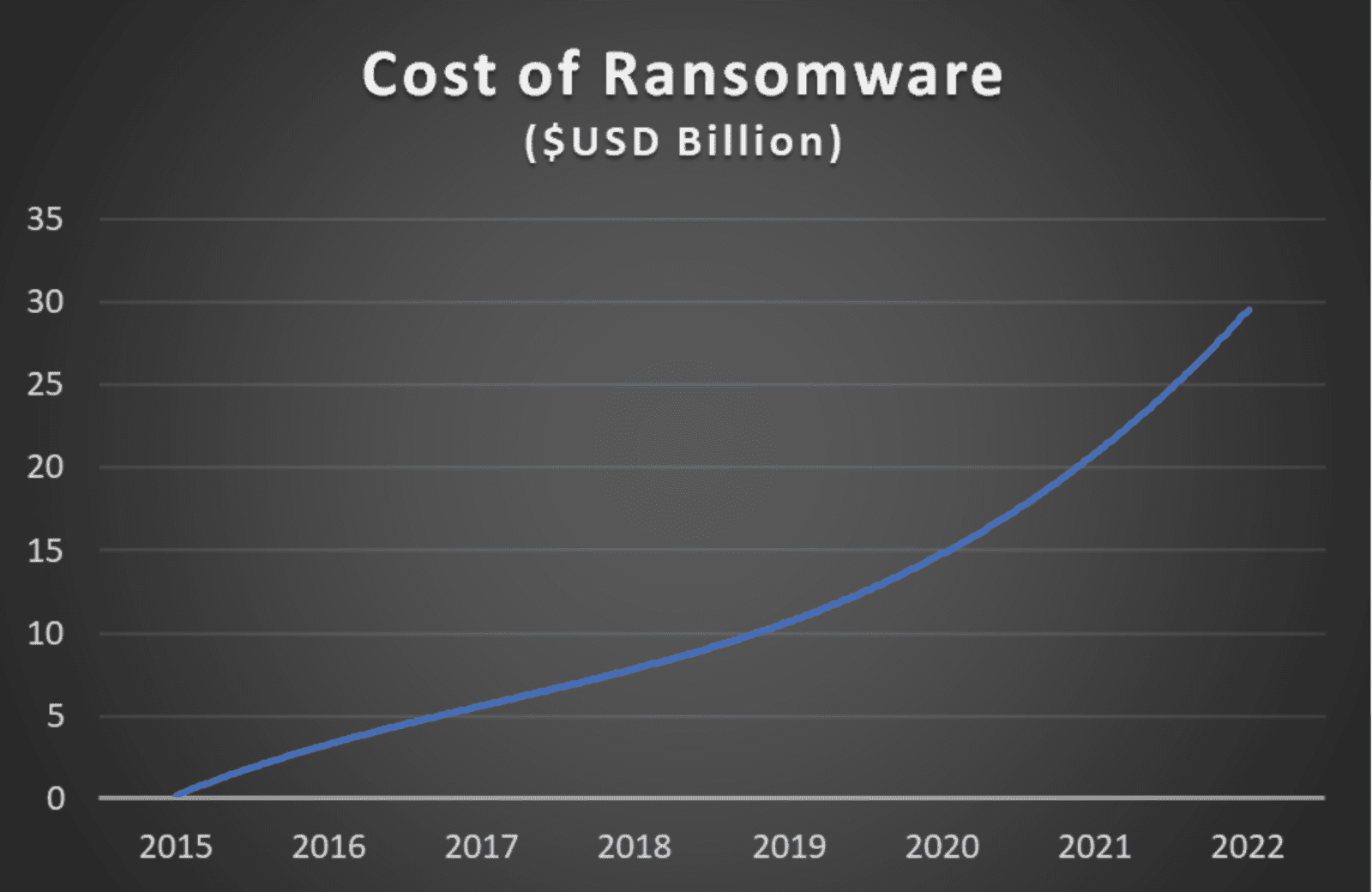
Figure 1: The skyrocketing cost of ransomware
It’s expected that the quantum of attacks will continue to increase almost exponentially over the next few years, as will the ruthlessness of some of the attackers.
This was foreshadowed in the recent Medibank attack in Australia, where medical records – neatly organised into “Nice” and “Naughty” lists, along with lists of women who had had abortions and much more – were released publicly.
Ransomware has evolved as well. As we saw in the NZX attacks, it’s not just about stolen data anymore, often it’s about using other approaches to knock businesses and infrastructure out unless you pay.
In fact, often these days there are 3 components to a ransomware attack:
- Encrypting data and closing systems, and refusing to unlock them unless a ransom is paid
- Taking of data and threatening to release it publicly, for example health records or intellectual property
- DDOS attacks on websites and infrastructure to encourage negotiation
Often businesses find themselves the victim of all three at once, and in a world of pain.
But according to the experts, things are only getting started. This trend is likely to continue over the next decade and it’s going to cost us all massively.

Hackers and Extortionists working together
One big trend in ransomware has been the advent of ransomware-as-a-service – essentially those gaining unauthorised access to systems working with experts at extortion.
This means a traditional “hacker” can simply pass on access to compromised systems to a ransomware group, who will handle the extortion and negotiations and they both get a payday.
This opens a whole new can of worms; while many attacks leading to ransom demands are still happening via traditional social or technical engineering, some are also coming from “inside jobs”, where disgruntled employees provide access to their employer’s networks to cash in on their access and/or pay back their employer for a perceived injustice.
The “as-a-service” model has also enabled specialist groups to focus on what they do best – it’s not uncommon for one group to gain access, another to manage the ransom negotiations, and another to provide DDOS attacks on-demand to reinforce the point.
Education and Healthcare are big targets
While attacks happen across all industries, we’re seeing the biggest increases across the Healthcare, Government, and Education sectors within both New Zealand and overseas.
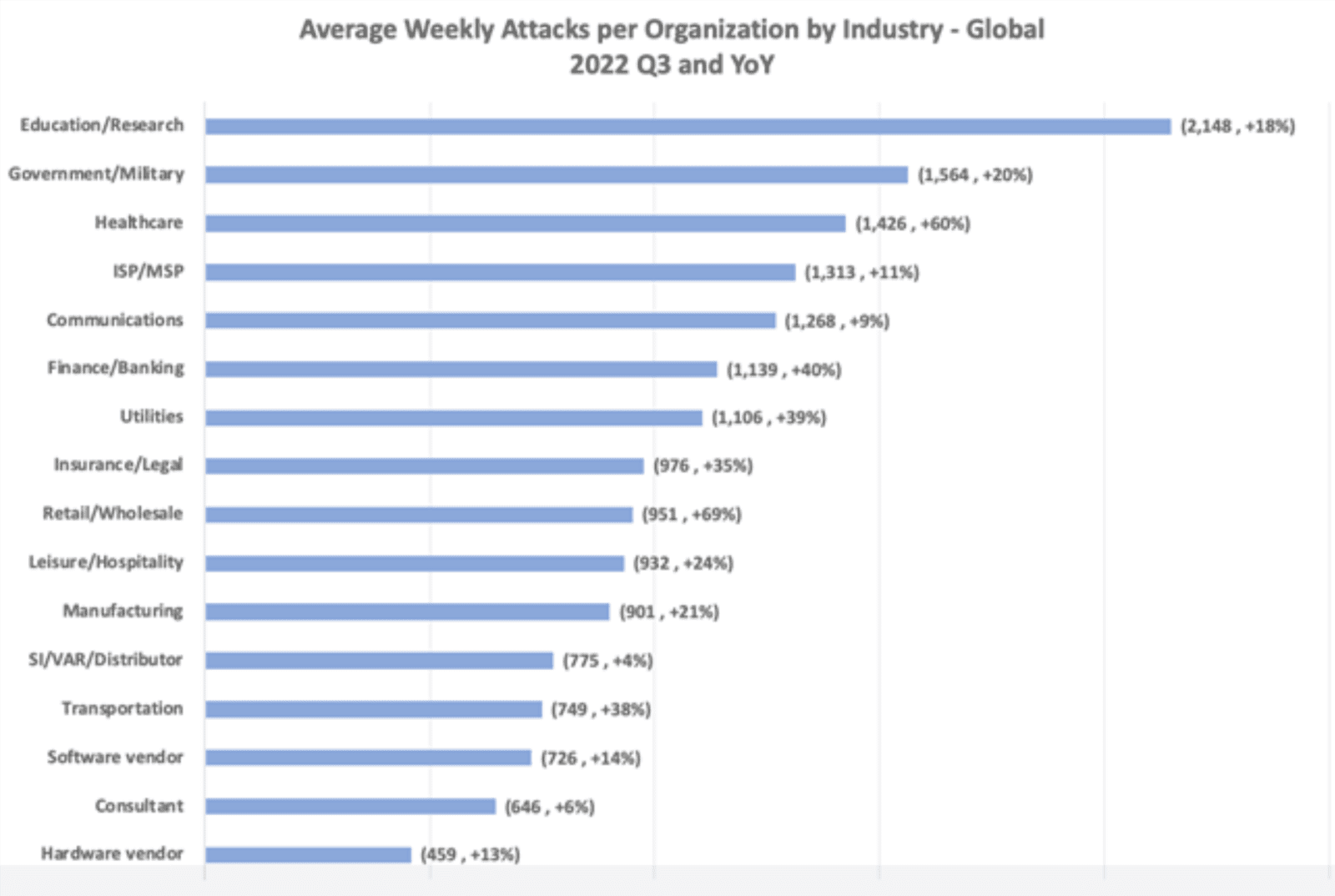
Figure 2: Weekly attacks by industry. Source: Check Point Research (2022)
The most prominent in recent times in New Zealand was the Waikato DHB, but many smaller health-related businesses are also regularly targeted.
Arguably, New Zealand will continue to be an attractive target while we lag behind other countries like Australia in both our national ability to deal with it, and our criminal laws and ability to bring people to justice.
We are currently poor at both, and the hackers know it.
This year, the Australian Federal Govt announced a $10 billion investment in cyber security, alongside stronger criminal sanctions. NZ spent a few million scattered here and there.
Destroying companies overnight
Many of those targeted by ransomware don’t survive. Whether they pay a ransom or not, the reputational and other damage is such that it’s game over.
Sometimes they do survive, but generally, only after spending the money they should have already spent hardening their systems. Medibank in Australia is a prime example of this, having battle-hardened their systems and being back online only now. Work they arguably should have done a long time ago.
In New Zealand, we’ve seen a series of high-profile attacks, such as 450,000 health records stolen from Pinnacle Health and released publicly, and the more recent Mercury IT attack that’s knocked out hundreds of organisations and government agencies.

Not pointing at any of these in particular, but in many cases, targeted companies didn’t take the precautions that you expect in this day and age. Many are held to account by relevant authorities for the social and financial cost that is borne by their customers as a result of this, but really – it’s too little, too late.
Hundreds if not thousands of New Zealand companies will be put out of business in the next few years due to ransomware attacks. Will you be one of them?
4 quick ways to stay safe
The reality is, nobody can stay 100% safe and secure from attack, however, there are certain key things that all businesses can do to stay as safe as possible:
1. Assume you will be attacked. Because chances are, you will. So if you’re going to be attacked then it follows that:
- You need to protect your customer’s data. Are your passwords encrypted? Are you only holding information you *really* need to hold? Are you encrypting data and storing it – and moving it – in as secure a manner as possible?
- You need to be ready. So when it happens, are you ready to deal with it? Do you have established relationships with experts to guide you through it? What policies do you need in place? Do you understand your legal obligations?
- You need a business continuity and disaster recovery plan. It’s all very well having a backup, but is it actually useful to you if your systems are out of action? What if your backup is compromised – what’s your failsafe? How can you get back online and your business operating again, quickly, once you’ve been attacked?
And if you can’t get your systems back up, how will you carry on carrying on?
2. Secure your systems. Properly. This means getting the experts in to both secure things, but then hammer them and try to get in. And no, your provider who set up your website or systems is NOT the person to attack it – get an external expert in.
If you haven’t had an independent security audit and pen-testing done this year, it’s been too long. Go get it sorted.
A decent audit won’t just look for possible ways in, but will also look at your whole infrastructure and recommend ways to secure it.
And remember, monitoring for intrusions is important – on an ongoing basis.
3. Remember Christmas is the best time for attacks. Many attacks occur during holidays as those charged with monitoring systems are often away. Keep an eye out. Consider closing down what you don’t need. Ensure everything is patched and up to date before disappearing off for a well-earned break.
4.Train your users! This one is often overlooked, but many attacks start with social engineering – gaining access through a legitimate user. Train your team on what to look out for. Run exercises. Talk about it a lot.
And a little bonus one that will help protect you for next time:
Never pay a ransom. Ever.

The only reason these attacks occur is that people pay them off. There’s a reason most governments won’t negotiate with terrorists.
For starters, you’re not guaranteed to get your data back (or prevent its public release). Secondly, it puts a target on your back for next time, but most importantly: it encourages the extortionists and makes it a viable business for them.
You owe it to the next company to not pay them off.
In summary
Ransomware is here to stay and there’s a good chance you’ll be impacted. You need to take steps now to ensure you’re both ready for when it happens, and as secure as you can be.
Things are getting nasty out there.
Paul Matthews is Chief Executive at CIO Studio. If you're concerned about your processes and infrastructure around cybersecurity, ring in the experts.
Get industry updates, tech news, and CIO Studio blogs free to your inbox!
